Enabling pull request reviews
About Minder's Pull Request Reviews
Minder ships with several rules that enable you to evaluate pull requests that add new dependencies to your projects.
- Check pull requests for vulnerable dependencies
(
stacklok/pr_vulnerability_check) - integrates with the osv.dev service to check if any newly added dependencies have a known vulnerability. If a new dependency is found to have known vulnerabilities, the pull request can be commented on with a summary of the CVEs found, marked as changes requested with an inline comment suggesting a fixed version, if available, or a commit status can be set to prevent the PR from being merged. - Check pull requests for dependencies with risk indicators from Stacklok
Insight (
stacklok/pr_vulnerability_check) - integrates with the Stacklok Insight service to comment on pull requests that add a dependency with configurable risk signals from Stacklok Insight and suggest an alternative.
Note that Minder is only able to review a PR if it's running under a different
user than the one that created the PR. If the PR is created by the same user,
Minder only provides a comment with the vulnerability information. An
alternative is to use the commit-status action instead of review where
Minder will set the commit status to failure if the PR introduces a new
vulnerability which can then be used to block the PR. This requires an
additional step though, where the repo needs to require the
minder.stacklok.dev/pr-vulncheck status to be passing.
Prerequisites
- The
minderCLI application - A Stacklok account - create one by logging into
the hosted Minder instance or by running
minder auth loginfrom the command line - A GitHub repository to be enrolled by Minder
Creating a Dependencies Security Profile From the UI
Start by logging in to Minder Cloud. In the left sidebar, select Profiles. Click New Profile, then select Dependency Security in the pop-up dialog. Finally click Apply.
The profile is now ready for use!
Taking the Dependencies Security Profile Into Use
Let's illustrate how the profile works, starting with the rule that checks for
known vulnerabilities. As an example, if we registered a Python repository and
opened a pull request that adds an old and vulnerable version of the popular
requests package, minder would have caught that the package is vulnerable and
replied with an inline comment:
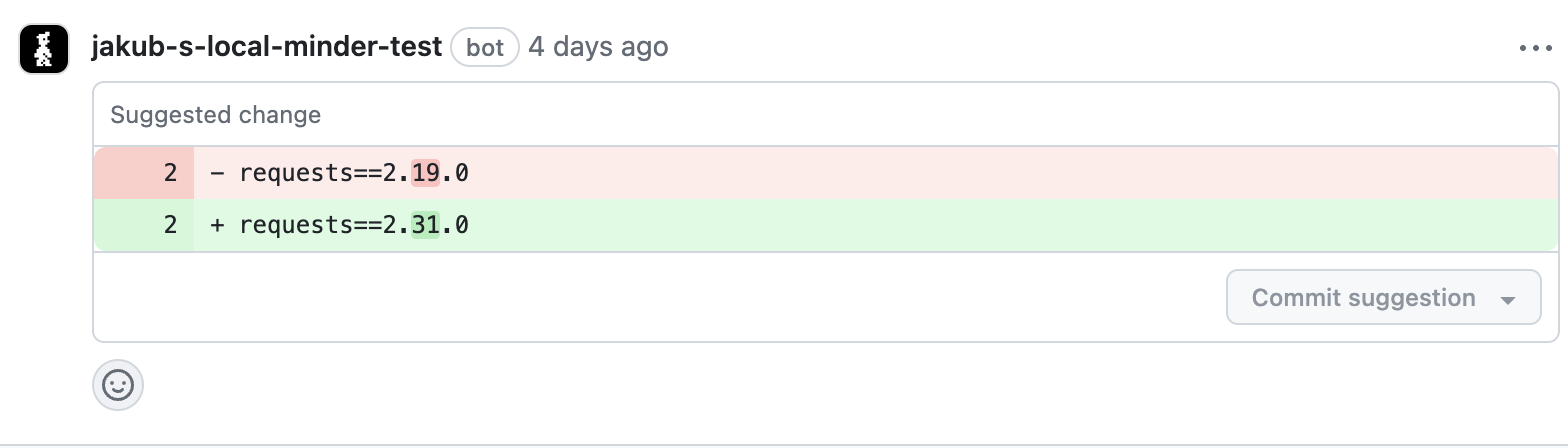
Note that Minder added an inline comment suggested the first version newer than the one submitted that doesn't have any CVEs. In addition, Minder requested changes on the pull request, preventing the pull request from being merged. This action is configurable and the configuration is discussed more below.
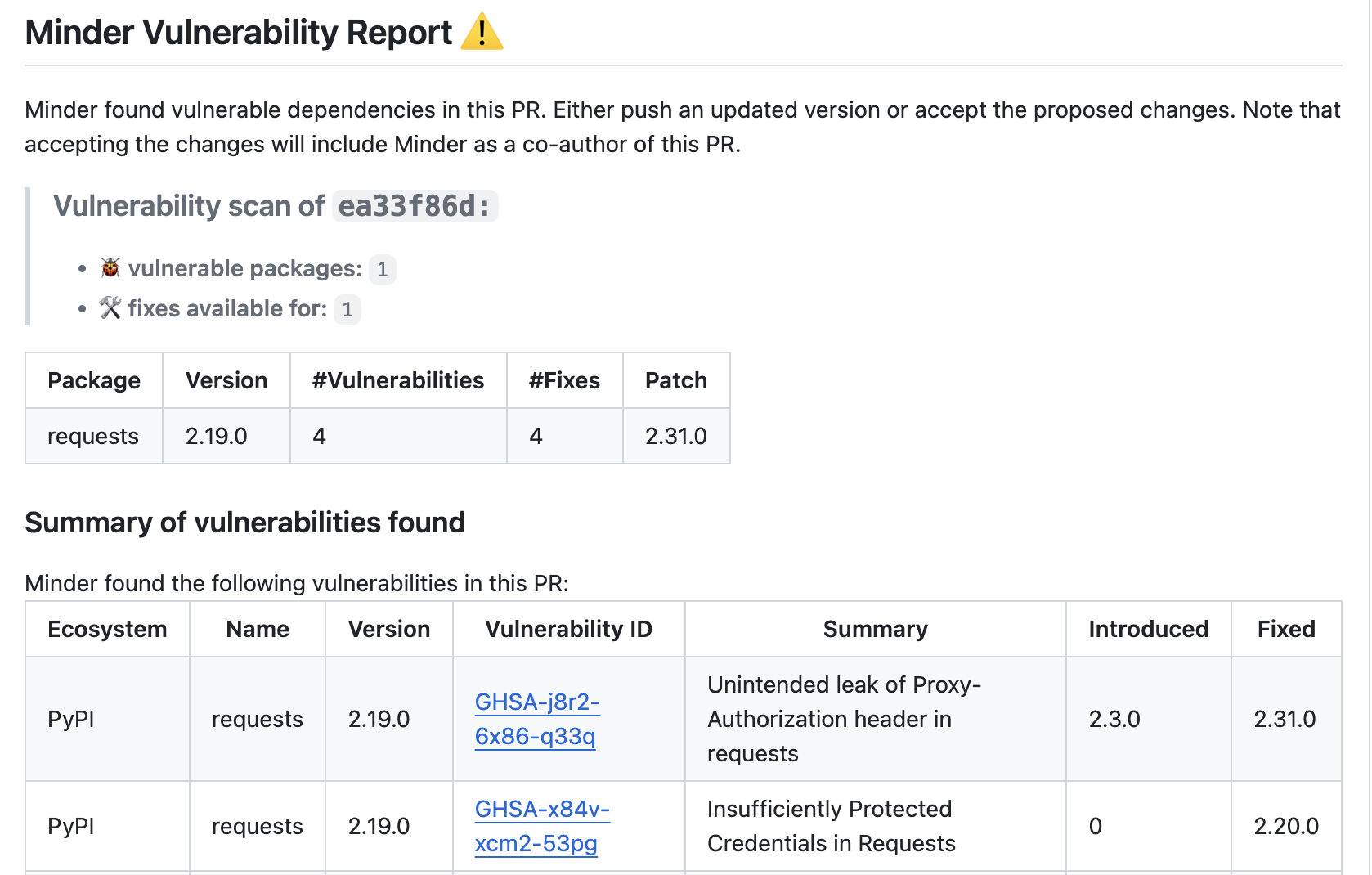
In addition to the inline review, minder always summarizes the vulnerabilities found, if any
 Similarly, if we opened a pull request to add a risky dependency against our
test Python project, the Stacklok Insight rule would have commented on the PR
and presented us with a list of alternatives, such as in this example that tried
to add the unmaintained
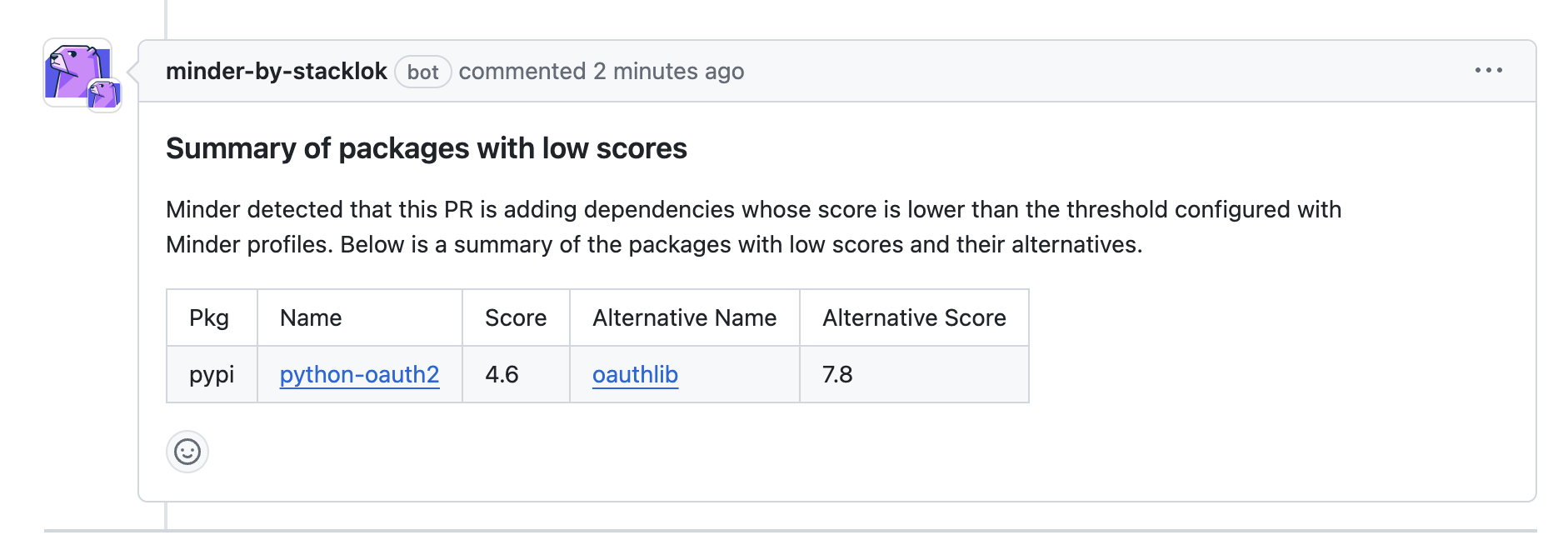
Similarly, if we opened a pull request to add a risky dependency against our
test Python project, the Stacklok Insight rule would have commented on the PR
and presented us with a list of alternatives, such as in this example that tried
to add the unmaintained python-oauth2 library as a dependency:
Creating a Dependencies Security Profile From the CLI
Create a new file called profile.yaml. Based on your source code language,
paste the following profile definition into the newly created file.
- Go
- NPM
- PyPI
---
version: v1
type: profile
name: pr-review-profile
context:
provider: github
alert: 'on'
remediate: 'off'
pull_request:
- type: pr_vulnerability_check
def:
action: review
ecosystem_config:
- name: go
vulnerability_database_type: osv
vulnerability_database_endpoint: https://api.osv.dev/v1/query
package_repository:
url: https://proxy.golang.org
sum_repository:
url: https://sum.golang.org
---
version: v1
type: profile
name: pr-review-profile
context:
provider: github
alert: 'on'
remediate: 'off'
pull_request:
- type: pr_vulnerability_check
def:
action: review
ecosystem_config:
- name: npm
vulnerability_database_type: osv
vulnerability_database_endpoint: https://api.osv.dev/v1/query
package_repository:
url: https://registry.npmjs.org
---
version: v1
type: profile
name: pr-review-profile
context:
provider: github
alert: 'on'
remediate: 'off'
pull_request:
- type: pr_vulnerability_check
def:
action: review
ecosystem_config:
- name: pypi
vulnerability_database_type: osv
vulnerability_database_endpoint: https://api.osv.dev/v1/query
package_repository:
url: https://pypi.org/pypi
Create the profile in Minder:
minder profile create -f profile.yaml
Once the profile is created, Minder will monitor any pull requests to the registered repositories. If a pull request brings in a dependency with a known vulnerability, then Minder will add a review to the pull request and suggest changes.
Alerts are complementary to the remediation feature. If you have both alert
and remediation enabled for a profile, Minder will attempt to remediate it
first. If the remediation fails, Minder will create an alert. If the remediation
succeeds, Minder will close any previously opened alerts related to that rule.